The hacktivist group R00TK1T has been increasingly targeting Malaysian infrastructure and organizations with a series of escalating cyber threats, as identified by CloudSEK, a cybersecurity firm specialising in digital risk monitoring.
Since November 2023, R00TK1T has intensified its operations in Malaysia, launching disruptive cyberattacks against various sectors such as telecommunications, education, and government entities, according to CloudSEK’s press release.
So far, the group has managed to infiltrate or attempted to infiltrate entities such as Maxis, Malaysia Airlines, the Federal Court of Malaysia, Malaysia’s water supply system, and the Youth and Sports Ministry, among others.
Timeline and Activities of R00TK1T in Malaysia
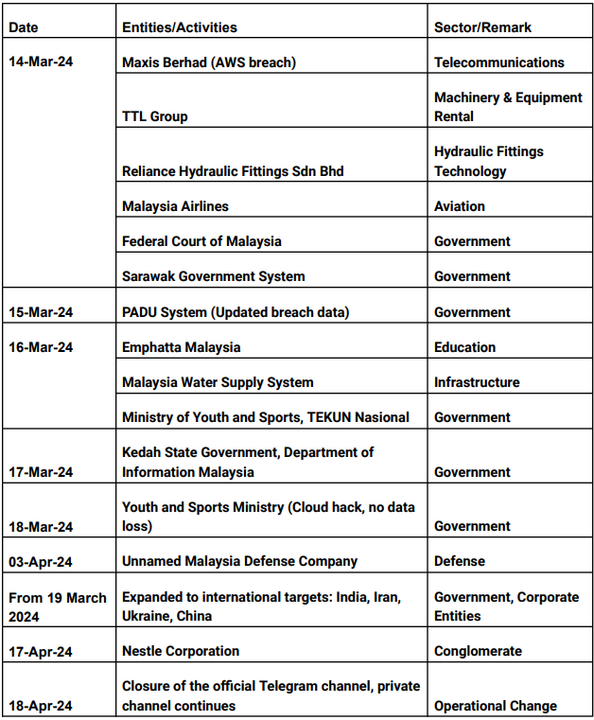
Primarily operating through its Telegram channel, R00TK1T ISC CYBER TEAM presents itself as a group of cyber mercenaries. Their main focus has been on critical infrastructure, with the intention of disrupting essential services and potentially instigating chaos.
Although the full extent of their technical capabilities remains uncertain, the successful attacks carried out in Malaysia showcase a level of sophistication in their methods.
CloudSEK’s investigation uncovered R00TK1T’s sophisticated capabilities, which encompass data exfiltration, targeting critical infrastructure, and exploiting zero-day vulnerabilities.
Of particular concern is the group’s utilisation of disgruntled employees, as revealed in Malaysia, where they purportedly leveraged insider information to their advantage.
CloudSEK recommends that organisations in Malaysia follow these steps to mitigate the risks posed by R00TK1T and any other hackers:
- Strong Backups and Recovery Systems: Ensure critical data and infrastructure have reliable backups to minimise downtime in case of an attack.
- Continuous Monitoring: Implement systems for ongoing monitoring of networks and systems to detect suspicious activity that may indicate a breach.
- Traffic Filtering and Absorption: Deploy tools capable of filtering and absorbing malicious traffic before it reaches critical systems, preventing denial-of-service attacks.
- Limited Access and Zero Trust: Restrict access to sensitive data using the principle of least privilege and enforce security protocols that mandate continuous verification before granting access, even within an organisation’s network.
- Clear Communication: Government agencies and trusted organisations should proactively communicate accurate information to counter misinformation spread by malicious actors.










